Introduction
At huntr, we take pride in showcasing the brilliant minds contributing to a safer, AI-powered world. Among our growing community of over 15,000 hackers and security researchers, Nguyen Van Hai (known as hainguyen0207) is making waves with his discoveries in AI/ML vulnerabilities. As a final-year student majoring in Information Security and an active contributor to huntr, Nguyen’s journey from web security to AI vulnerability hunting is surely one to listen to. In this spotlight, we explore how Nguyen’s passion for bug bounty hunting led him to uncover vulnerabilities on the huntr platform.
Meet hainguyen0207
My name is Nguyen Van Hai (also known as hainguyen0207). I'm currently a final-year student at the Academy of Cryptography Techniques in Vietnam, majoring in Information Security. I am currently working at BlueCyber LLC.
I recently started exploring the field of cybersecurity and was fortunate enough to discover a vulnerability on the huntr platform. This experience has fueled my passion for the field, and I'm eager to deepen my expertise and contribute to making the digital world safer.
How did you get into AI/ML bug bounty hunting? What parts of it do you enjoy?
I had known about the huntr platform for a while and had explored and found vulnerabilities there. However, in October 2023, when huntr announced its shift in focus to open-source AI software, I decided to step away and move to other platforms. At the time, I thought AI was something incredibly complex, and finding vulnerabilities in it seemed almost impossible. But then, a colleague of mine, @vn-ncvinh, told me he had successfully discovered vulnerabilities in AI/ML on huntr. That reignited my passion, and I returned to the platform, choosing LOLLMS as my first program to dive into. The initial steps were challenging, but with the guidance and support of @vn-ncvinh, I managed to find my first AI-related vulnerability on huntr.
What I enjoy most about this journey is the process of reading and analyzing source code. It allows me to uncover fascinating insights. Additionally, reviewing reports from other researchers has been incredibly beneficial to my growth.
How did you discover huntr and what has your journey been like?
I discovered the huntr platform in June 2023, right after finishing my third year at university. At that time, I had just started my journey into the field of Information Security, focusing particularly on web security. I spent a lot of time learning about common vulnerabilities such as SQL Injection, XSS, CSRF, and IDOR… finding these issues both fascinating and challenging.
During this period, a like-minded friend, introduced me to the huntr platform—at that time, huntr had not yet shifted its focus to AI. This was a pivotal moment in my learning journey, as I was fortunate enough to discover my first vulnerability on the platform soon after. The thrill of finding that vulnerability not only brought me immense satisfaction but also fueled my motivation, affirming the path I had chosen. Huntr became not only a place to test my skills but also a source of inspiration that continues to drive me to explore and grow in the field of bug bounty hunting.
And thanks to that, I had a good interview and got accepted to BlueCyber LLC, where I met talented, friendly, and dedicated colleagues: @vn-ncvinh, @duongli99, @domiee13, @ngductung, and @boyqb2212.
Uncovering Path Traversal Vulnerabilities in parisneo/lollms: hainguyen0207's Case Study
Recently, hainguyen0207 uncovered a path traversal vulnerability in parisneo/LOLLMS, an open-source AI software designed to facilitate the development and deployment of large language models (LLMs) through a flexible and user-friendly interface. While many researchers had already explored the project and identified several vulnerabilities, hainguyen0207 decided to take a deeper look at the source code, hoping to find something that others may have missed.
Let's have hainguyen0207 take the wheel and show you his step-by-step process in discovering and exploiting this vulnerability.
Step-by-Step Process
Discovery Phase: Identifying the Vulnerability
When I accessed the lollms_configuration_infos.py file, I saw something strange.
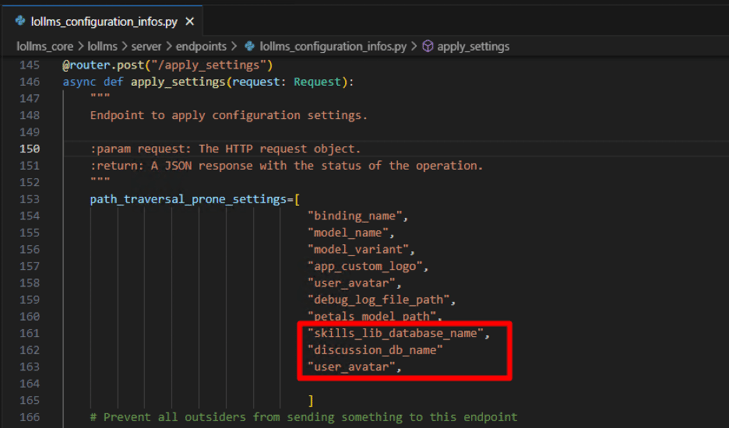
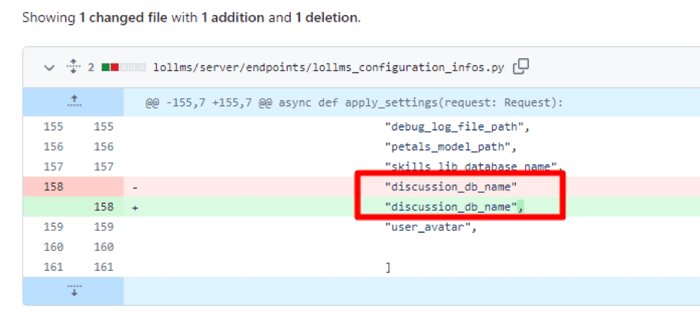
Yes, that's right, the discussion_db_name and user_avatar elements in the path_traversal_prone_settings array are missing the ",". This is a programming error.

Next, I reviewed how the path_traversal_prone_settings array elements are passed as parameters to the sanitize_path function.
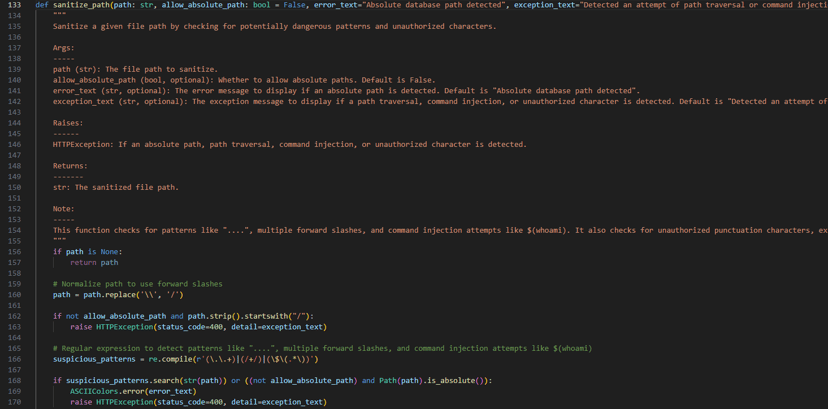
After reviewing the sanitize_path function, it was clear that its purpose is to filter user input by blocking characters such as .., /, and \\ to prevent path traversal vulnerabilities. It was evident that the programmer's intention was to protect against these types of attacks. However, the lack of a trailing comma in the path_traversal_prone_settings array left the discussion_db_name and user_avatar fields still vulnerable to exploitation.
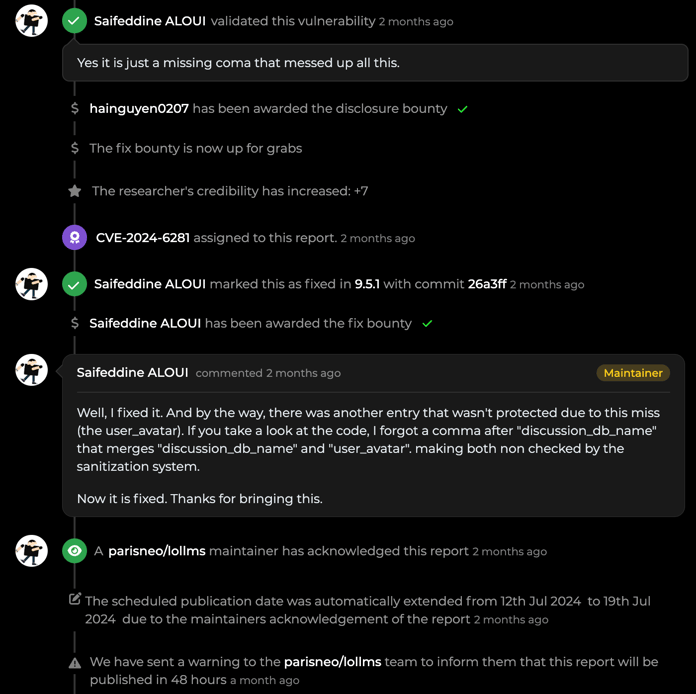
The Impact of Nguyen Van Hai’s Vulnerability Report on LOLLMS
Here’s a step-by-step overview of how I tested and confirmed the vulnerability:
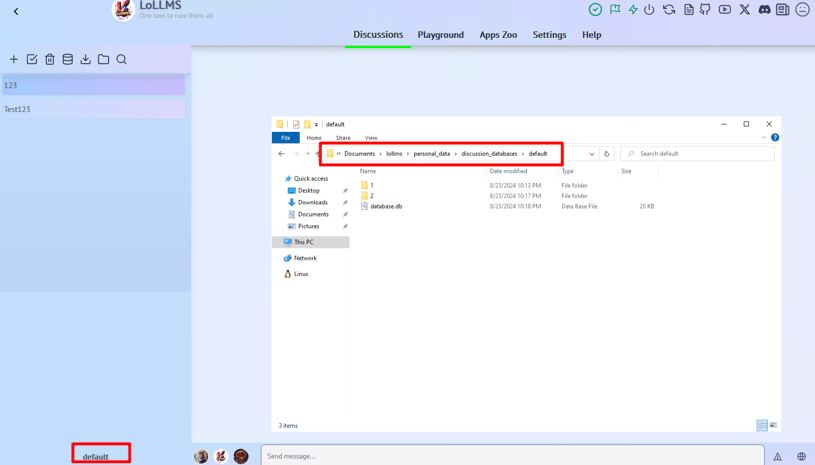
1. Launch LOLLMS and access the default setup path for the database.
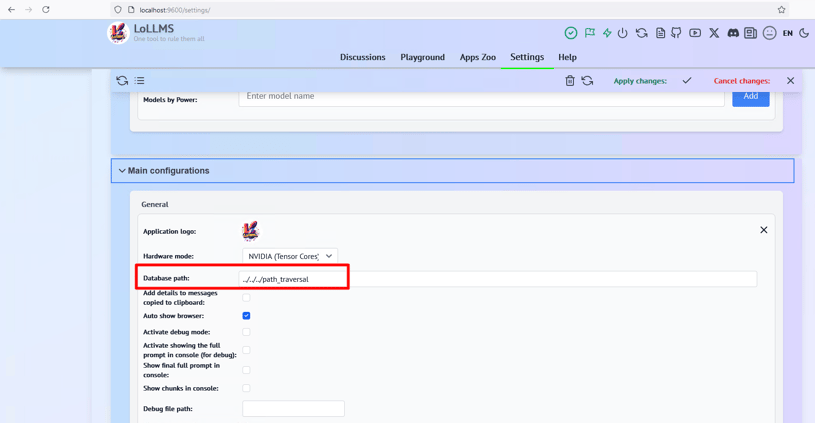
2. See default setup path of Database path.
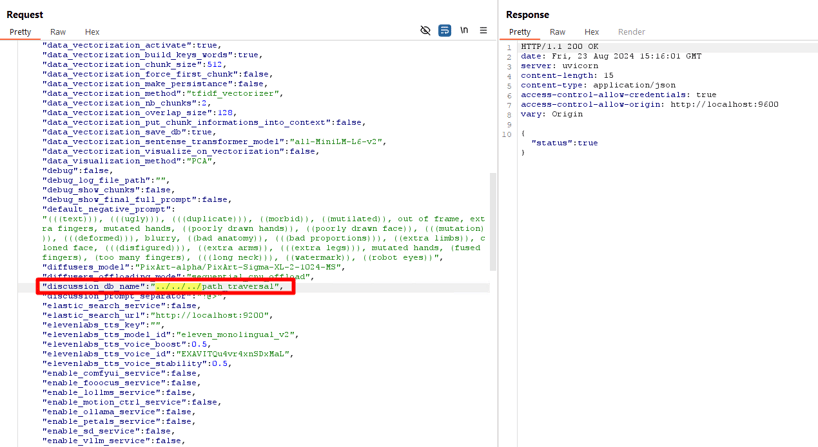
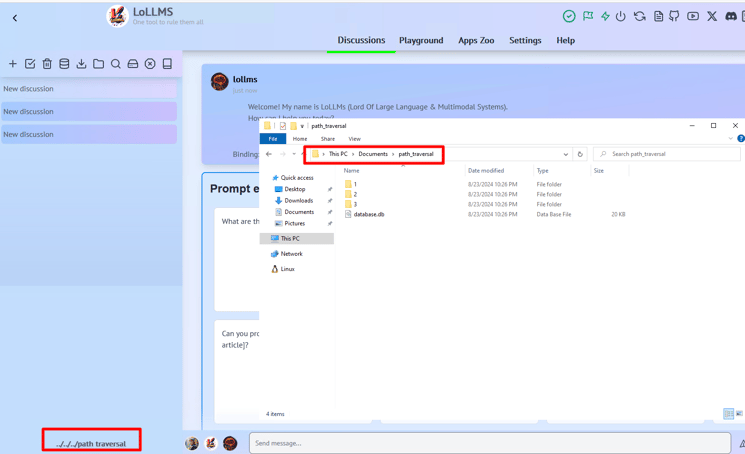
3. Go to Settings and insert a payload into the Database path: ../../../path_traversal.
How a Simple Code Fix Secured LOLLMS Against Path Traversal Attacks
This vulnerability could have allowed attackers to alter the database path, potentially overwriting folders and files on the victim’s machine.
After reporting it, the LOLLMS maintainer quickly resolved the issue by simply adding the missing comma to the path_traversal_prone_settings array—demonstrating how small errors can lead to significant vulnerabilities.
Join the Huntr Community: Start Your AI/ML Bug Hunting Journey
Feeling inspired by Nguyen Van Hai’s journey? Join huntr's community of hackers, researchers, and tech enthusiasts dedicated to securing the future of AI and open-source software. Whether you're a seasoned professional or just beginning your bug bounty adventure, there's a place for you here. Tap into valuable resources like the Beginner's Guide to AI/ML Bug Hunting and start your own path to discovering and fixing vulnerabilities with huntr today!


