Introduction
At huntr, we love to celebrate the incredible talent in our community who are helping secure the future of AI/ML systems. Today, we’re excited to spotlight Ileana Barrionuevo, known as @acciobugs on huntr, from Córdoba, Argentina. In this blog, we’ll dive into Ileana’s journey into AI/ML bug bounty hunting, her experience with huntr, and how she recently discovered an Improper Access Control vulnerability in the lunary-ai/lunary project—allowing unauthorized privilege escalation and manipulation of projects across different organizations.
Meet acciobugs
Hi, I'm Ileana Barrionuevo (@acciobugs) from Córdoba, Argentina! I work as a security engineer and also teach Secure Software Development at the Universidad Tecnológica Nacional - Facultad Regional Córdoba. As a security researcher, I focus on web and mobile vulnerabilities. I’m a big fan of CTFs and enjoy speaking at InfoSec conferences. Last year, I had the incredible experience of speaking at DEFCON for the first time!
How did you get into AI/ML bug bounty hunting? What parts of it do you enjoy?
I'm a big fan of code review, so when I saw new AI/ML projects to analyze on huntr, I thought it was worth checking if security had been considered, especially since many are used by big companies. I was surprised to discover basic security bugs, which made it clear that these projects need serious code inspection!
I particularly enjoy deploying the project locally, debugging the app to understand its behavior, and conducting a black-box pentest. I then complement that analysis with white-box testing, as I have access to the source code.
How did you discover huntr and what has your journey been like?
I discovered this platform in October 2020 and began testing various GitHub repositories. At first, I thought finding security bugs through source code would be too difficult. But then I shifted my approach and decided to run a project locally just to see what would happen—and I don’t regret it.
Understanding why things work the way they do is key to helping developers resolve these issues, which is why I love spending my free time hunting for vulnerabilities in the source code!
Uncovering Improper Access Control Vulnerabilities in lunary-ai/lunary: A Deep Dive by acciobugs
Recently, @acciobugs identified a significant Improper Access Control (CWE-284) vulnerability in lunary-ai/lunary, an open-source platform designed to manage AI projects across multiple teams. This vulnerability allowed users to manipulate project and user assignments across different organizations, leading to unauthorized privilege escalation.
Here’s a look into @acciobugs' journey in finding and exploiting this vulnerability.
What Can an Attacker Do?
Due to improper backend controls, a member with team management permissions could:
- A) Manipulate user invites to force users into joining projects from other organizations.
- B) Change team members to other organizations' projects, escalating their privileges.
- C) Move other organization's users into projects under their own control or another project, allowing unauthorized privilege escalation.
This was all possible because the backend did not properly validate project identifiers when performing these actions, leaving the system open to abuse.
Step-by-Step Process
Let’s focus on case C, which demonstrates how an attacker can manipulate other organization members into joining different projects and escalate their privileges.
1. Play with the platform and understand how it works.
The platform's structure manages:
Organization > Project > Owner > Team members (Admins, Viewers, Prompt Editors, etc.).
2. Send a request to change a member from another organization to a project that doesn’t belong to them, or even into a project from your own organization. By modifying the project identifier in the request, you can assign roles such as Admin or Owner to that user, giving them full permissions in the project.
Here’s the modified request:
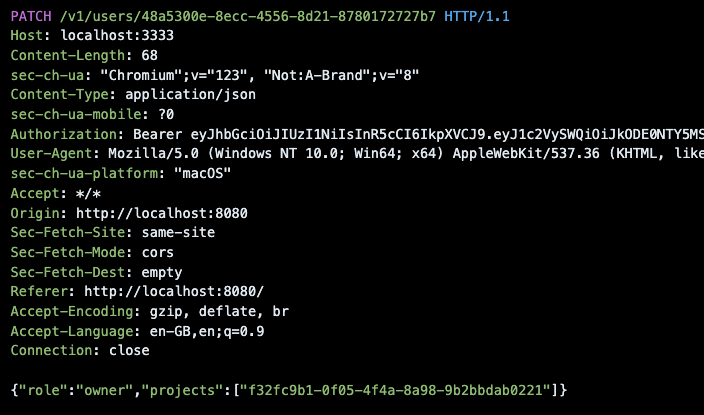
3. See the changes applied.
After sending the request, the platform accepts the project changes without validating the user's organization. The affected user ends up in a project they don’t own, and the attacker successfully escalates their privileges to an Admin or Owner role.
Here’s the result:

And we can see the the user ends up associated to a project in OUR org:

The Impact
This vulnerability allowed malicious actors to manipulate users across organizations, creating significant inconsistencies and security risks. By escalating privileges to roles like Admin or Owner, attackers could gain unauthorized access to projects, posing a severe threat to the platform’s integrity.
Root Cause: Flaws in Backend Validation
The issue was rooted in the backend’s failure to validate project IDs in the request:
- The project ID is taken from the request but is not validated against the authenticated user's organization, allowing attackers to add users to unauthorized projects.
for (const projectId of projects) {
await sql`
insert into account_project (account_id, project_id) values (${user.id}, ${projectId}) returning *
`
}----
- The project IDs from the requests are not validated against the projects of the authenticated user's organization, allowing arbitrary insertion of members into projects.
for (const projectId of projects) {
await sql`
insert into account_project (account_id, project_id)
values (${userId}, ${projectId})
on conflict (account_id, project_id)
do nothing
`
}
ctx.status = 200
ctx.body = { message: "User updated successfully" }--
Conclusion
Thanks to @acciobugs’ report, the lunary-ai/lunary team was able to address this vulnerability quickly, preventing further exploitation. This case highlights how improper access control can lead to serious security issues, emphasizing the need for strict backend validation in multi-organization platforms.
Join the Huntr Community: Start Your Bug Hunting Journey
Feeling inspired by @acciobugs' impressive find? Join huntr’s community of hackers, researchers, and tech enthusiasts committed to securing AI and open-source software. Whether you're a seasoned pro or just getting started in bug hunting, there's a place for you here. Explore our Beginner’s Guide to AI/ML Bug Hunting and start uncovering vulnerabilities with huntr today!


